How Digital Ocean Handles DDoS Attacks and Security Threats
Kicking off with How Digital Ocean Handles DDoS Attacks and Security Threats, this opening paragraph is designed to captivate and engage the readers, setting the tone casual formal language style that unfolds with each word.
The content of the second paragraph that provides descriptive and clear information about the topic
Overview of Digital Ocean's approach to handling DDoS attacks and security threats
Digital Ocean employs a proactive approach to handling DDoS attacks and security threats by implementing robust security measures to protect their cloud services. The company understands the critical importance of safeguarding their infrastructure and customer data from malicious attacks.
The Importance of Robust Security Measures in Cloud Services
Security is a top priority for cloud service providers like Digital Ocean due to the sensitive nature of the data stored on their platforms. Implementing robust security measures helps prevent unauthorized access, data breaches, and potential service disruptions.
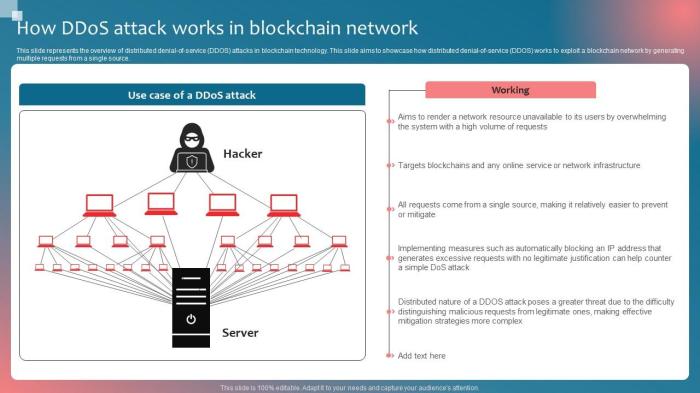
Challenges Specific to DDoS Attacks and Security Threats in the Cloud Environment
DDoS attacks pose a significant threat to cloud services by overwhelming servers with a flood of traffic, leading to downtime and potential data loss. In the cloud environment, the challenge lies in defending against these attacks while ensuring minimal disruption to service for legitimate users.
Digital Ocean's DDoS mitigation techniques

When it comes to mitigating DDoS attacks, Digital Ocean employs a range of sophisticated techniques to protect their infrastructure and customers.
Traffic Scrubbing and Filtering
Digital Ocean uses advanced traffic scrubbing and filtering techniques to identify and block malicious traffic during a DDoS attack. This helps ensure that legitimate traffic can still reach its intended destination without disruption.
Anycast Technology
With the use of Anycast technology, Digital Ocean is able to distribute incoming traffic across multiple data centers, making it easier to absorb and mitigate the impact of DDoS attacks. This helps in maintaining uptime and availability for their customers.
Rate Limiting and Traffic Shaping
By implementing rate limiting and traffic shaping mechanisms, Digital Ocean can control the flow of traffic to their network, preventing overwhelming amounts of data from causing disruptions. This helps in maintaining a stable and secure environment for their services.
Security protocols and measures implemented by Digital Ocean
Digital Ocean takes security very seriously and has implemented several protocols and measures to safeguard against various security threats. This includes encryption methods to protect user data, access control mechanisms, and authentication protocols.
Encryption Methods
- Digital Ocean uses strong encryption algorithms to secure user data both in transit and at rest.
- The data is encrypted using industry-standard protocols such as SSL/TLS to ensure secure communication between users and the Digital Ocean platform.
- Encryption keys are managed securely and access is restricted to authorized personnel only.
Access Control Mechanisms
- Access to sensitive data and systems within Digital Ocean is strictly controlled through role-based access control (RBAC).
- Multi-factor authentication (MFA) is enforced to add an extra layer of security for user accounts.
- Regular audits and monitoring are conducted to detect any unauthorized access attempts and prevent security breaches.
Authentication Protocols
- Digital Ocean implements strong authentication protocols such as OAuth and OpenID Connect to verify the identity of users accessing the platform.
- User passwords are securely stored using hashing algorithms to prevent unauthorized access to user accounts.
- Real-time authentication checks are performed to ensure that only legitimate users are granted access to sensitive data and resources.
Incident response and monitoring at Digital Ocean
When it comes to incident response and monitoring at Digital Ocean, the company has established robust procedures to handle security incidents promptly and effectively. These procedures are crucial in ensuring the safety and integrity of the network and data.
Incident Response Procedures
- Digital Ocean follows a structured incident response plan that Artikels the steps to be taken in the event of a security incident. This includes identifying the nature and scope of the incident, containing the threat, investigating the root cause, and implementing remediation measures.
- Upon detection of a security incident, Digital Ocean's security team promptly responds to mitigate the threat, minimize potential damage, and restore normal operations as quickly as possible.
- The incident response team conducts thorough post-incident analysis to learn from the incident, improve security measures, and prevent similar incidents in the future.
Network Monitoring for Threats
- Digital Ocean employs advanced monitoring tools and technologies to continuously monitor its network for potential security threats. These monitoring systems analyze network traffic, detect anomalies, and alert security personnel to investigate any suspicious activities.
- Real-time monitoring allows Digital Ocean to proactively identify and respond to potential security threats before they escalate into major incidents. This proactive approach helps in maintaining a secure environment for its customers.
Role of Automation in Incident Response
- Automation plays a significant role in incident response and threat detection at Digital Ocean. Automated systems are used to monitor network traffic, analyze security logs, and identify patterns indicative of potential security threats.
- Automated incident response tools help in quickly detecting and responding to security incidents, reducing response times, and minimizing the impact of security breaches. This efficient use of automation enhances the overall security posture of Digital Ocean's infrastructure.
Ultimate Conclusion

The content of the concluding paragraph that provides a summary and last thoughts in an engaging manner
Question & Answer Hub
What are the main strategies Digital Ocean uses to handle DDoS attacks?
Digital Ocean employs a combination of traffic filtering, rate limiting, and network layer protection to mitigate DDoS attacks effectively.
How does Digital Ocean differentiate between legitimate traffic and DDoS attacks?
Digital Ocean uses advanced algorithms and traffic analysis techniques to distinguish between normal traffic patterns and malicious DDoS attacks.
What security protocols does Digital Ocean have in place to protect against security threats?
Digital Ocean implements strong encryption methods, access control mechanisms, and authentication protocols to safeguard against various security threats.
How does Digital Ocean respond to security incidents?
In case of a security incident, Digital Ocean follows predefined procedures, conducts thorough investigations, and takes necessary actions to mitigate risks and prevent future occurrences.




